Cyberattackers mimic government websites in phishing emails using templates
Bad actors have seized coronavirus as a way to scam people online
Get all the latest news on coronavirus and more delivered daily to your inbox. Sign up here.
Cyberattackers have been mimicking government websites in phishing emails related to the coronavirus pandemic with ready-made templates, according to a new study by cybersecurity company Proofpoint.
Bad actors have seized coronavirus as a way to get people to share their personal information online using a cyberattack method called "phishing" in which scammers create fraudulent email addresses and websites to trick curious users into giving up sensitive information or downloading viruses.
In the last two months, these actors have been caught creating more and more fake websites related to COVID-19 information, including financial assistance, using templates that make their sites look identical to real, government platforms to target victims.
"These templates enable a threat actor of less sophisticated technical abilities to launch a well-crafted credential phishing attack," Sherrod DeGrippo, Proofpoint's senior director of threat research and detection, told FOX Business. "Threat actors can then lure their targets into clicking links that lead to these pages."
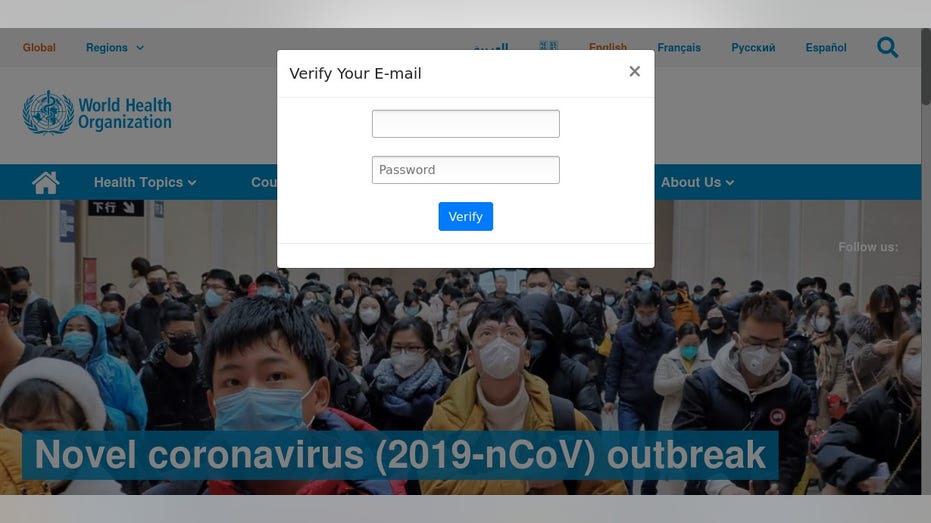
WHO template/ Proofpoint study
Proofpoint discovered templates imitating the World Health Organization (WHO), Internal Revenue Service (IRS), Centers for Disease Control (CDC), the United Kingdom government, the government of Canada, and the government of France.
Bad actors will often send emails to people using legitimate-looking email addresses claiming to offer things like a coronavirus vaccine or extra stimulus cash. The emails will then ask users to click on a link, which often leads to a fraudulent website like those discovered by Proofpoint that use templates to make their webpages look legitimate.
CORONAVIRUS SCAMS: A LOOK AT SCHEMES BUSTED BY THE FBI
Fraudulent websites will then ask users to input sensitive information such as credit card information and phone numbers, which bad actors can steal and use.
DeGrippo said the campaigns Proofpoint discovered could have reached "a few dozen targets to hundreds of thousands of targets." She also said the templates were all launched separately rather than in a joint attack.
"Distribution typically operates between threat actors directly, and transactions can occur through underground marketplaces at varying costs. Some threat actors make and use these templates, others generate them and sell them. There are similar credential phishing kits available for use for free," she explained.
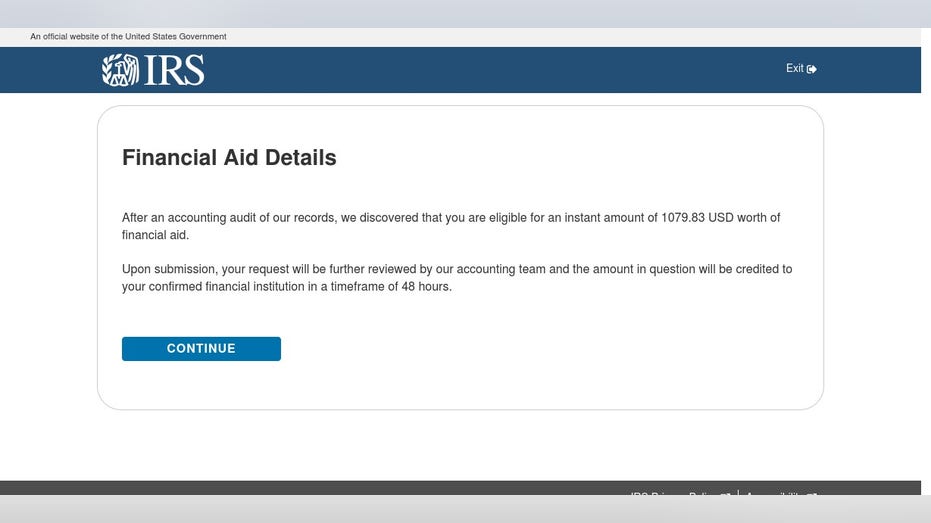
Use of these templates surged in March and have gradually tapered off, likely because of "a combination of saturation for COVID-19 payment theme phishing templates and a move towards other COVID-19 themes as many one-time payments were disbursed," the blog post explained.
FBI WARNS OF SCAMMERS TARGETING CORONAVIRUS FEARS
Bad actors often seize popular trends and word events to catch potential victims' attention and information through phishing emails.
"Threat actors worldwide continue to follow the news surrounding the COVID-19 pandemic and adapt their themes to try and take advantage of human vulnerabilities, fears, and concerns, which are shared across countries," DeGrippo said. "It's clear that threat actors are localizing phishing lures to particular countries through native language, stolen branding of local institutions, and social engineering around concerns and fears specific to their region."
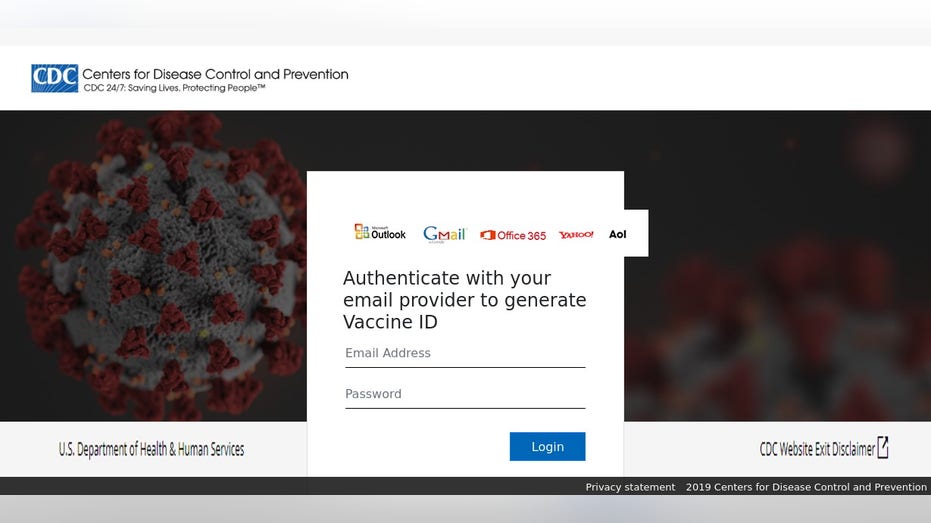
Proofpoint's template discoveries highlight cybercriminals who are willing to pay money for pre-made designs to more effectively capture targets in their efforts to gain access to people's credentials.
GET FOX BUSINESS ON THE GO BY CLICKING HERE
Cybersecurity research company Check Point Research's 2020 Global Threat Index similarly found that cyberattackers were taking advantage of the pandemic as early as February.
Domain names on self-made websites involving coronavirus-related words jumped at the time and have been increasing ever since. Hackers have also used COVID-19 relief checks as a way to get potential victims' attention in phishing emails to get a hold of people's sensitive information.
DeGrippo said users can protect themselves from these phishing attempts by being "extremely vigilant when confirming the source of all emails that are sent to their inboxes."
CLICK HERE TO READ MORE ON FOX BUSINESS
"Typical giveaways are unsolicited emails urgently requesting a link be clicked, a password change, or transfer of money. Watch for misspelling, fraudulent display names, and fake sender email addresses. If the email looks suspicious, skip the link and type in the address of the actual page," she said.




















